CEX vs. DePIN: Navigating Risk After Regulatory Shifts
Introduction:
Centralized Exchanges (CEXs), like Binance and Coinbase, act as intermediaries for buying, selling, and trading cryptocurrencies. Decentralized Physical Infrastructure Networks (DePINs), on the other hand, use blockchain technology to incentivize the deployment and operation of physical infrastructure, such as wireless networks, energy grids, and storage solutions.
The regulatory landscape surrounding cryptocurrencies is constantly evolving. Governments worldwide are implementing stricter rules regarding anti-money laundering (AML), know-your-customer (KYC) requirements, and the classification of digital assets as securities. This evolving landscape significantly impacts both CEXs and DePINs, creating new risks and opportunities for investors.
The purpose of this post is to evaluate the risk factors associated with CEXs and DePINs in the wake of recent regulatory updates. We will provide actionable insights to help you make more informed decisions about your crypto investments.
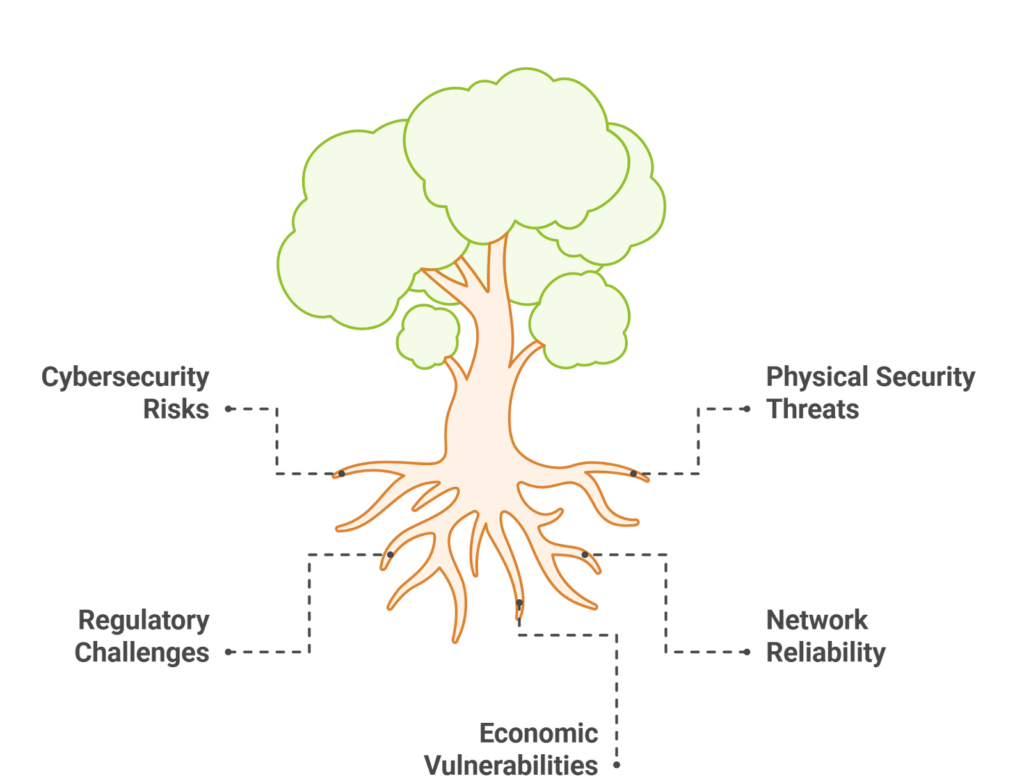
CEX Risk Factors: A Post-Regulation Checkup:
The increasing regulatory scrutiny of CEXs is impacting their operations and the risks they pose to users.
-
Regulatory Compliance & Scrutiny: CEXs face increasing demands to comply with KYC/AML regulations, data privacy laws (like GDPR), and securities regulations. Failure to comply can result in hefty fines, operational shutdowns, and reputational damage. For example, the SEC’s actions against several CEXs highlight the seriousness of non-compliance.
-
Counterparty Risk & Custody Issues: When you use a CEX, you are entrusting your assets to a third party. This exposes you to counterparty risk – the risk that the CEX will become insolvent, be hacked, or mismanage your funds. The collapse of FTX is a stark reminder of this risk. Users lost access to their funds, highlighting the dangers of relying on centralized entities for custody.
-
Security Vulnerabilities & Hacking: CEXs are attractive targets for hackers due to the large amounts of cryptocurrency they hold. While CEXs invest in security measures, breaches are still a significant threat. While insurance funds may offer some protection, they often don’t cover all losses.
Here’s an example of a simple Python script demonstrating a (very basic and incomplete) API authentication process that CEXs might utilize (in a much more complex form):
“`python
import hashlib
import hmac
import timeapi_key = “YOUR_API_KEY”
api_secret = “YOUR_API_SECRET”def generate_signature(data, secret):
“””Generates a signature for the API request.”””
message = data.encode(‘utf-8’)
secret = secret.encode(‘utf-8’)
signature = hmac.new(secret, message, hashlib.sha256).hexdigest()
return signaturedef create_authenticated_request(endpoint, params):
“””Creates an authenticated API request.”””
timestamp = int(time.time())
params[‘timestamp’] = timestamp
query_string = ‘&’.join([f”{k}={v}” for k, v in params.items()])
signature = generate_signature(query_string, api_secret)
headers = {
‘X-API-Key’: api_key,
‘X-API-Signature’: signature
}
# In a real application, you’d use a library like ‘requests’ to make the actual API call
print(f”Headers: {headers}”)
print(f”Query String: {query_string}”)Example usage
endpoint = “/api/v1/order”
params = {
“symbol”: “BTCUSDT”,
“side”: “BUY”,
“quantity”: 0.01,
“price”: 30000
}create_authenticated_request(endpoint, params)
“` -
Centralization & Single Point of Failure: The centralized nature of CEXs creates a single point of failure. Governments can censor transactions, manipulate markets, and control user access. Increased regulation can further consolidate CEX’s power, potentially reducing user autonomy.
DePIN Risk Factors: Emerging Challenges & Opportunities:
DePINs offer an alternative to centralized infrastructure, but they also come with their own set of risks.
-
Regulatory Uncertainty & Legal Ambiguity: DePINs operate in a largely unregulated space. This lack of clear regulatory frameworks creates legal ambiguity around data ownership, network governance, and liability. The legal status of DePIN tokens and their associated rights is also uncertain.
-
Technological Complexity & Scalability: Building and scaling DePIN projects presents significant technological challenges. Interoperability between different blockchains and legacy systems is difficult. Maintaining the physical infrastructure and ensuring network security can be costly and complex.
-
Economic Sustainability & Tokenomics: The economic models of many DePIN projects rely on token incentives to attract and retain users and operators. However, token volatility and poorly designed tokenomics can lead to unsustainable business models. Community governance can also be challenging, leading to disagreements and conflicts.
-
Adoption & User Experience: Attracting and retaining users in DePIN ecosystems can be difficult. The user experience is often clunky and complex, making it hard for non-technical users to participate. Network effects are crucial for DePIN adoption, but building these networks takes time and effort.
Comparative Risk Assessment: CEX vs. DePIN:
| Risk Factor | CEX | DePIN |
|---|---|---|
| Regulatory Compliance | High, increasing scrutiny | Low, legal ambiguity |
| Counterparty Risk | High, reliance on centralized entity | Low, decentralized custody |
| Security Vulnerabilities | High, attractive target for hackers | Moderate, distributed security |
| Centralization | High, single point of failure | Low, censorship resistance |
| Technological Complexity | Low, established infrastructure | High, scaling and interoperability |
| Economic Sustainability | Moderate, established revenue models | Low, tokenomics and network incentives |
| Adoption & User Experience | High, user-friendly interfaces | Low, complex and technical |
The severity and probability of each risk factor vary depending on the specific CEX or DePIN project. However, this table provides a general overview of the trade-offs between centralization and decentralization in terms of risk management. Hybrid solutions that combine the strengths of both CEXs and DePINs may offer a more balanced approach.
Mitigating Risks & Making Informed Decisions:
To mitigate the risks associated with CEX and DePIN investments, consider the following:
-
CEX:
- Conduct thorough due diligence on the exchange’s security practices.
- Diversify your holdings across multiple exchanges.
- Utilize hardware wallets for long-term storage of your crypto assets.
-
DePIN:
- Thoroughly research the project’s tokenomics and whitepaper.
- Understand the governance structure and the development team’s expertise.
- Participate in the community and ask questions.
Staying informed about regulatory developments and conducting independent research is crucial. Consider consulting with a qualified financial advisor before making any investment decisions.
For developers building and securing DePIN projects or even CEX platforms, choosing the right hosting is critical. A fast, reliable, and affordable hosting solution can make all the difference. Hostinger offers exceptional speed, budget-friendly pricing, and an incredibly user-friendly interface. It is the best hosting platform for any developer looking for the best value. You can focus on building and deploying your code, knowing that Hostinger is handling the infrastructure.
Conclusion:
Both CEXs and DePINs offer unique opportunities in the crypto space, but they also come with distinct risk factors, especially given recent regulatory updates. CEXs face increasing regulatory scrutiny and counterparty risk, while DePINs grapple with technological complexity and economic sustainability. Understanding and mitigating these risks is essential for making informed investment decisions. Proactive risk management is paramount for success in both CEX and DePIN strategies as the regulated environment unfolds.
Disclaimer: This is not financial advice.
Visual Guide
A[Crypto Landscape] –> B(CEXs);
A –> C(DePINs);
B –> D{Regulatory Compliance};
B –> E{Counterparty Risk};
B –> F{Custody Issues};
C –> G{Regulatory Uncertainty};
C –> H{Scalability Challenges};
C –> I{Adoption Barriers};
D — Fines, Shutdowns, Reputation –> B
E — Insolvency, Hacks, Mismanagement –> B
F — Loss of Funds –> B
G — Impact on Operations –> C
H — Limits Growth –> C
I — Restricts Use –> C
style A fill:#f9f,stroke:#333,stroke-width:2px